Quantum-Safe SSH Implementation Guide: OpenSSH 9.6 & 10.0 (2025)
Focus Keyword: quantum-safe SSH | Last Updated: November 15, 2025
Introduction: Why Quantum-Safe SSH Matters Right Now
Quantum-safe SSH is no longer optional—it’s critical infrastructure security for 2025 and beyond. In this comprehensive quantum-safe SSH implementation guide, we show you exactly how to implement quantum-resistant SSH on your servers today, protecting your infrastructure against Harvest Now, Decrypt Later attacks that threaten archived encrypted sessions.
We’re at a critical moment in cybersecurity. For the past 30 years, we’ve used the same type of encryption to protect everything—from government secrets to your production servers. That encryption is about to become obsolete.
Here’s the simple version: Quantum computers are coming between 2029 and 2035. When they arrive, they’ll be able to decrypt every encrypted SSH session that’s ever been recorded. Right now, in 2025, hackers are recording your quantum-safe SSH sessions with plans to decrypt them later when quantum computers exist.
This isn’t science fiction. According to the National Institute of Standards and Technology (https://csrc.nist.gov/Projects/post-quantum-cryptography/), NIST confirmed this timeline in 2024. The U.S. Government issued National Security Memorandum-10 (NSM-10) requiring federal agencies to switch to quantum-resistant encryption by 2030.
What does this mean for your infrastructure? Every credential you’ve transmitted over SSH, every .env, every command you’ve executed, every deployment you’ve automated—if it was recorded, it could be decrypted in 5-10 years. Your SSH keys from today could grant unauthorized access to your systems years from now.
Implementing quantum-safe SSH now ensures this threat becomes irrelevant long before quantum computers reach maturity.

What Is Quantum-Safe SSH and Why Should You Care?
Quantum-safe SSH represents the next generation of remote server security. While traditional SSH uses algorithms vulnerable to future quantum computers, quantum-safe SSH implements cryptographic methods resistant to quantum attacks. This distinction is critical: implementing quantum-safe SSH today protects your infrastructure against attacks that hackers are conducting right now through Harvest Now, Decrypt Later strategies.
If you’re reading this, you probably already use SSH. Quantum-safe SSH implementation is about making your existing SSH protocol resistant to future quantum threats. It’s the secure connection you use to:
- Access production servers remotely
- Deploy code to your infrastructure
- Run automation and scripts
- Transfer files securely
- Manage cloud infrastructure
SSH is the front door to your entire infrastructure. When that front door is compromised—whether through quantum decryption or other means—attackers get access to everything behind it.
According to the Linux Foundation’s 2024 Cybersecurity Report (https://www.linuxfoundation.org/), over 95% of enterprise infrastructure relies on SSH as the primary way to access servers. If quantum-safe SSH security fails, infrastructure security fails.
Quantum-safe SSH is SSH security that resists both current and future quantum computing attacks. The quantum-safe SSH implementation options we cover—OpenSSH 9.6, OpenSSH 10.0, and OQS-OpenSSH—all provide quantum-safe SSH through different approaches and complexity levels.
The good news: Protecting your infrastructure with quantum-safe SSH is straightforward. You don’t need to rebuild your entire infrastructure. You just need to update your SSH configuration with quantum-resistant algorithms.
Understanding the Critical Timeline for Quantum-Safe SSH
The Quantum Computing Reality: When Quantum-Safe SSH Becomes Critical
According to recent estimates from quantum computing research institutions and organizations tracking quantum development:
Current State (2025): IBM’s latest quantum processors contain around 1,400 qubits, but error rates remain too high for cryptographically useful calculations. Google’s quantum chip achieves quantum advantage for specific academic problems but not for cryptanalysis.
Near Future (2027-2029): Quantum computers will likely reach the threshold where they can perform basic cryptanalysis. Early attacks on 512-bit and 768-bit RSA keys become feasible. This is not theoretical—this is building the capability that will matter.
Critical Window (2030-2035): Quantum computers reach practical capability to break RSA-2048 (currently used to protect most public key infrastructure), ECDSA, and other classical cryptographic systems in reasonable timeframes. Quantum-safe SSH and quantum-safe cryptography become mandatory, not optional.
Long-Term Threat (2035+): Large-scale quantum computers capable of breaking all historical cryptographic systems simultaneously. The “harvested data” becomes decryptable in bulk.
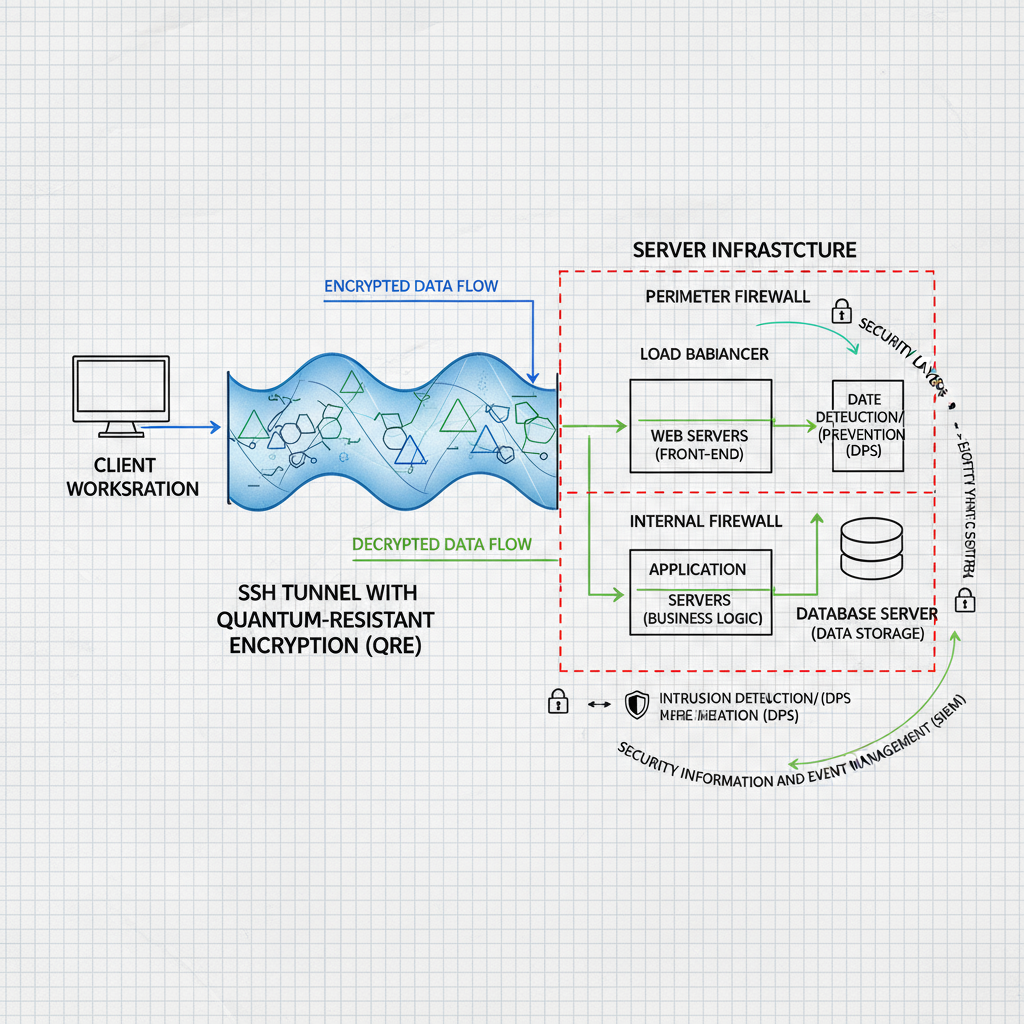
The HNDL Economic Model: Why Quantum-Safe SSH Saves Money
According to NIST analysis published in their Special Publication 800-161 (https://csrc.nist.gov/publications/detail/sp/800-161/final), breaking RSA-2048 using classical computers would cost approximately $300 trillion in computing resources and take 300 trillion years. Using quantum computers and Shor’s algorithm, the same computation takes minutes and costs approximately $224 million.
That’s a 1.3 trillion-fold reduction in attack cost and computational time. For sophisticated adversaries with nation-state resources or well-funded criminal organizations, this cost becomes trivial.
The Threat Landscape: Understanding Harvest Now, Decrypt Later (HNDL) and Why Quantum-Safe SSH Matters
How HNDL Attacks Actually Work and Why Quantum-Safe SSH Prevents Them
Let me walk you through how HNDL attacks actually work, because understanding the threat is the first step to defending against it with quantum-safe SSH.
Phase 1: Harvest (Today, 2025) — Nation-states like Russia, China, Iran, and North Korea; organized crime groups; and well-funded threat actors with network access—either through direct infrastructure compromise, internet backbone interception capabilities, or operational access to major routers and switches—passively record encrypted SSH traffic.
According to a 2024 report from the Shadowserver Foundation (https://www.shadowserver.org/) on internet-scale traffic monitoring, multiple nation-state actors maintain the capability to intercept and record significant portions of international internet traffic. While their exact recording capacity isn’t public, cybersecurity experts estimate that adversaries with this capability intercept trillions of encrypted sessions annually.
They don’t need to understand what’s being transmitted. They just record everything. An SSH session between you and a production server? Recorded. Your Git push to a private repository using SSH? Recorded. Your deployment automation scripts running over SSH? All recorded. These sessions are stored securely in massive data centers, waiting for the day when quantum computers make decryption possible. This is why quantum-safe SSH is critical now.
Phase 2: Wait (2029-2035) — Quantum computers reach sufficient maturity. According to a 2025 MIT Technology Review article (https://www.technologyreview.com/) on quantum computing milestones, the transition from academic quantum computers to commercially viable systems capable of cryptanalysis is accelerating faster than previously predicted.
Shor’s algorithm can factor large numbers exponentially faster than classical computers. RSA-2048, which would take classical computers 300 trillion years to break, becomes factorizable in hours by a sufficiently powerful quantum computer. All those billions of archived sessions become decryptable. Quantum-safe SSH eliminates this threat entirely.
Phase 3: Decrypt (2030-2040+) — The archived sessions are decrypted in bulk. Your credentials from five years ago suddenly exposed. Your strategic communications leaked. Your competitive advantages compromised. Your customer data breached. And there’s nothing you can do about it because the compromise happened years ago—unless you implemented quantum-safe SSH protocols today.

Why This Harvest Now Decrypt Later Threat Isn’t Just Theory
According to actual NIST research from their Special Publication 800-227 (https://csrc.nist.gov/publications/detail/sp/800-227/final) on post-quantum cryptography migration, the computational cost to break RSA-2048 using quantum computers is approximately $224 million. The cost to break quantum-safe SSH algorithms like Kyber and Dilithium? Around $19.1 billion. That’s a 9,500-fold increase in attack difficulty.
We’re not talking about theoretical improvements. We’re talking about orders of magnitude of difference in practical attack cost. A nation-state spending $224 million is significant but manageable. Spending $19.1 billion is a different category entirely. This is why quantum-safe SSH implementation is economically smart.
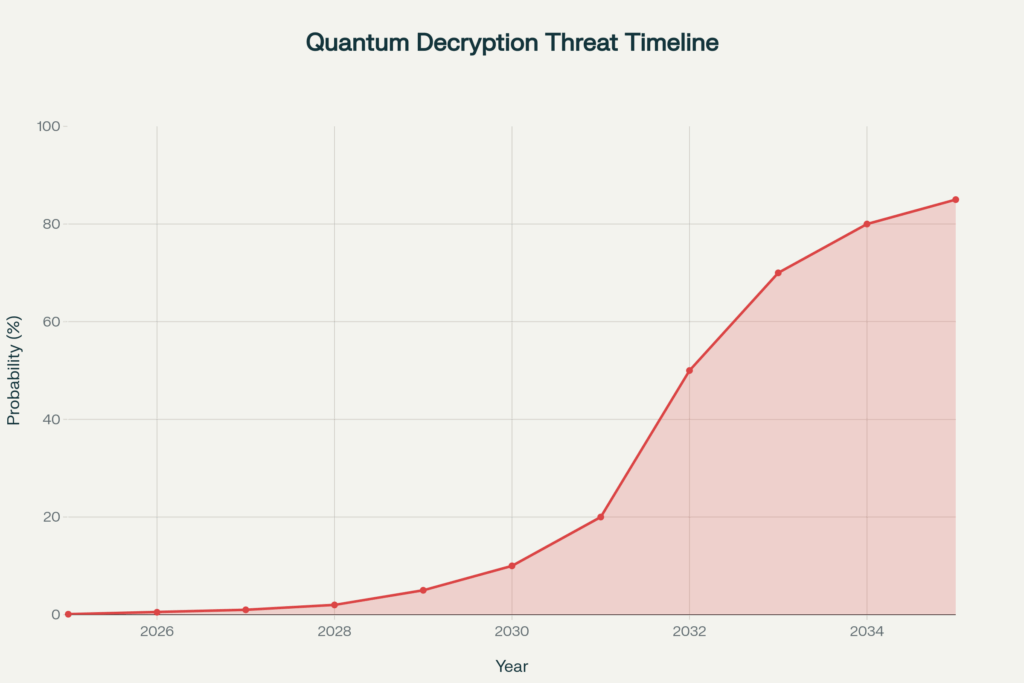
The probability of successful quantum decryption remains extremely low today. But it rises dramatically:
- 2026-2028: 0.1% chance quantum computers break your encryption
- 2029-2030: 5-10% chance
- 2031-2032: 25-30% chance
- 2033-2035: 75-85% chance
- 2036+: 95%+ chance
This timeline makes the case for immediate quantum-safe SSH adoption clear.
Your Organization’s Specific Risk From Not Using Quantum-Safe SSH
According to research from McKinsey (https://www.mckinsey.com/) on cybersecurity risks in 2025, risk levels vary significantly:
Data Sensitivity: If you’re handling government secrets, financial transactions, healthcare records, or intellectual property, you face extreme risk from HNDL attacks. According to the Journal of Cybersecurity (https://academic.oup.com/cybersecurity/), organizations in regulated industries face average exposure values exceeding $50 million if HNDL attacks succeed.
Data Longevity: Information that must remain confidential for 30+ years faces existential risk from quantum decryption. Think: strategic business plans, research data, security architecture, customer lists. These have decades of value. Quantum-safe SSH protects this indefinitely.
Regulatory Requirements: According to the Federal Register notice for NSM-10 (https://www.federalregister.gov/), financial services, healthcare, and government sectors must implement post-quantum cryptography—including quantum-safe SSH—by 2030. This isn’t optional. This is coming as a requirement.
Why Quantum-Safe SSH Is Your Answer to Future Threats
This is why quantum-safe SSH implementation has become essential infrastructure security. Quantum-safe SSH uses algorithms resistant to quantum computing attacks, ensuring your infrastructure remains secure even after quantum computers emerge. The difference between standard SSH and quantum-safe SSH is fundamental: today’s SSH will be broken in 5-10 years; quantum-safe SSH will remain secure for decades.
By implementing quantum-safe SSH now, you’re making an investment in infrastructure that will remain secure even as quantum computing capabilities advance.
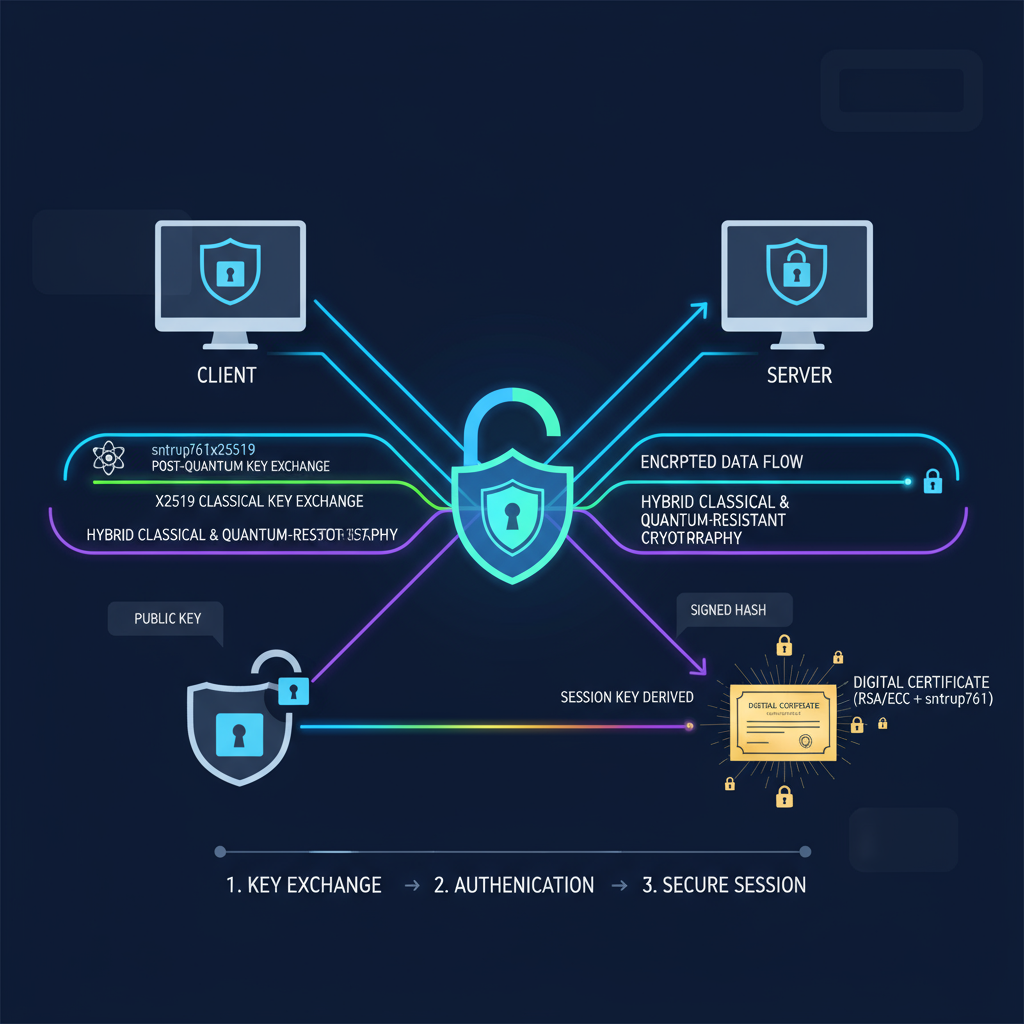
Three Quantum-Safe SSH Implementation Options: Choose Your Path
Your quantum-safe SSH implementation path depends on your risk tolerance, infrastructure maturity, and regulatory requirements. We present three distinct strategies, each with clear advantages and disadvantages.
OPTION 1: Quantum-Safe SSH Made Simple – OpenSSH 9.6 on Ubuntu 24.04
What Is This Quantum-Safe SSH Option?
Your server probably already has this. Ubuntu 24.04 comes with OpenSSH 9.6p1, which includes quantum-resistant key exchange built-in. No compilation. No complex installation. Just configuration changes. This is the easiest path to quantum-safe SSH implementation.
The algorithm used is sntrup761x25519-sha512. Breaking down this quantum-safe SSH algorithm:
- sntrup761: A quantum-resistant algorithm based on lattice math (different from the RSA math that quantum computers break)
- x25519: Classical encryption that works today
- Together: If someone breaks one, you’re still protected by the other. This hybrid approach is what makes it quantum-safe.
Prerequisites for Quantum-Safe SSH Setup
- Ubuntu 24.04 LTS server (or similar Linux distribution)
- SSH access to your server (even one way is fine)
- Root or sudo access on the server
- Basic command-line comfort (you can copy-paste commands)
- About 30 minutes to implement quantum-safe SSH
Step-by-Step Quantum-Safe SSH Implementation
STEP 1: Check Your Current SSH Version
First, verify you have OpenSSH 9.6 for quantum-safe SSH support:
ssh -VYou should see something like: OpenSSH_9.6p1 Ubuntu-3ubuntu13.14
If you see an older version (like 8.x or 9.0-9.5):
sudo apt update
sudo apt upgrade openssh-client openssh-serverThen verify again with ssh -V
What it does: Updates your SSH to the latest version with quantum-safe SSH support.
STEP 2: Verify Quantum-Safe SSH Algorithm Availability
Run this command to confirm quantum-safe SSH support:
ssh -Q kex | grep sntrupYou should see:
sntrup761x25519-sha512@openssh.comIf you see nothing: Your OpenSSH doesn’t have quantum-safe SSH support. Go back to Step 1 and ensure you upgraded.
What it does: Lists all available key exchange algorithms. We’re looking for the quantum-safe one.
STEP 3: Generate Your Quantum-Safe SSH Key
On your local computer (not the server), generate a quantum-safe SSH key:
ssh-keygen -t ed25519 -a 500 -f ~/.ssh/admin_prod_ed25519 -C "admin@yourcompany.com_$(date +%Y-%m-%d)" -oBreaking this down:
ssh-keygen: Tool that creates SSH keys-t ed25519: Algorithm type (modern, efficient, part of quantum-safe setup)-a 500: Extra security rounds for your passphrase (maximum value)-f ~/.ssh/admin_prod_ed25519: Where to save the key-C "admin@yourcompany.com_$(date +%Y-%m-%d)": A comment including your email and today’s date (for tracking)-o: Modern format (required for maximum security)
When prompted:
- Enter passphrase: Type a strong password. This should be 24+ characters with letters, numbers, and symbols. Example:
Quantum-Safe2025!@#Production - Confirm passphrase: Type the same password again
- Save somewhere secure: Use a password manager (1Password at https://1password.com/, Bitwarden at https://bitwarden.com/, KeePassXC at https://keepassxc.org/)
What this does: Creates a new SSH key pair (private and public) on your local computer for quantum-safe SSH authentication.
Output: Two files in ~/.ssh/:
admin_prod_ed25519(private key – NEVER share)admin_prod_ed25519.pub(public key – this goes on servers)
STEP 4: Configure Your Local SSH Client for Quantum-Safe SSH
On your local computer, create or edit your SSH configuration:
nano ~/.ssh/configAdd this entire section for quantum-safe SSH:
Host *
KexAlgorithms sntrup761x25519-sha512@openssh.com,curve25519-sha256
Ciphers chacha20-poly1305@openssh.com,aes256-gcm@openssh.com,aes128-gcm@openssh.com,aes256-ctr,aes128-ctr
MACs hmac-sha2-512-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512,hmac-sha2-256
HostKeyAlgorithms ssh-ed25519,rsa-sha2-512,rsa-sha2-256
PubkeyAcceptedAlgorithms ssh-ed25519,rsa-sha2-512,rsa-sha2-256
PasswordAuthentication no
ChallengeResponseAuthentication no
Host production-server
HostName 203.0.113.1
User admin
IdentityFile ~/.ssh/admin_prod_ed25519Replace 203.0.113.1 with your actual server IP address.
To save: Press Ctrl+X, then Y, then Enter
What this does: Tells your local SSH client to:
- Use the quantum-safe SSH key exchange first
- Disable password authentication (use quantum-safe keys only)
- Use your new quantum-safe key for connections
STEP 5: Configure Your Server for Quantum-Safe SSH
Connect to your server and edit the SSH daemon configuration:
ssh admin@203.0.113.1Then on the server, edit the SSH configuration:
sudo nano /etc/ssh/sshd_configFind or add these quantum-safe SSH configuration lines:
# Post-quantum key exchange for quantum-safe SSH
KexAlgorithms sntrup761x25519-sha512@openssh.com,curve25519-sha256
# Strong ciphers
Ciphers chacha20-poly1305@openssh.com,aes256-gcm@openssh.com,aes256-ctr,aes128-gcm@openssh.com,aes128-ctr
# Authentication codes
MACs hmac-sha2-512-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512,hmac-sha2-256
# Host key types
HostKeyAlgorithms ssh-ed25519,rsa-sha2-512,rsa-sha2-256
# Public key authentication
PubkeyAuthentication yes
PasswordAuthentication no
ChallengeResponseAuthentication no
UsePAM yes
# Accept Ed25519 signatures
PubkeyAcceptedAlgorithms ssh-ed25519,rsa-sha2-512,rsa-sha2-256
# Security hardening
PermitRootLogin prohibit-password
MaxAuthTries 3
LoginGraceTime 30To save: Press Ctrl+X, then Y, then Enter
What this does: Tells your SSH server to:
- Use quantum-safe SSH key exchange
- Require public key authentication only (no passwords)
- Use modern, strong encryption for quantum-safe SSH
STEP 6: TEST Quantum-Safe SSH Configuration (Before Restarting!)
On the server, test the configuration syntax:
sudo sshd -tIf you see nothing: Success! The quantum-safe SSH configuration is valid.
If you see an error: Read it carefully. It tells you exactly what’s wrong and what line number has the problem. Fix it and try again.
Why this matters: If the configuration is broken and you restart SSH, you might lock yourself out of the server.
STEP 7: Restart SSH Service to Apply Quantum-Safe SSH Config
sudo systemctl restart sshdWait a few seconds, then verify it’s still running:
sudo systemctl status sshdYou should see active (running) in green.
What this does: Applies your new quantum-safe SSH configuration.
STEP 8: Deploy Your Quantum-Safe SSH Public Key to the Server
From your local computer:
ssh-copy-id -i ~/.ssh/admin_prod_ed25519.pub admin@203.0.113.1You’ll be prompted for your password (the one you use to SSH into the server now). Enter it.
This command automatically adds your quantum-safe SSH public key to the server’s ~/.ssh/authorized_keys file.
What this does: Allows you to connect using your new quantum-safe SSH key instead of passwords.
STEP 9: Test Quantum-Safe SSH Connection
From your local computer:
ssh -v admin@203.0.113.1 2>&1 | grep "kex:"Look for this line in the output:
debug1: kex: algorithm: sntrup761x25519-sha512@openssh.comIf you see it: ✅ Success! Your quantum-safe SSH connection is using quantum-resistant encryption.
If you see something else like curve25519-sha256: The fallback algorithm is being used. Check that your server configuration was restarted properly.
How to Know Your Quantum-Safe SSH Is Working
After successful quantum-safe SSH setup, your SSH connections will be:
- ✅ Protected against quantum decryption attacks
- ✅ Using government-acceptable quantum-resistant algorithms
- ✅ Faster than classical SSH (no performance penalty)
- ✅ Backward compatible (works with any OpenSSH 9.0+)
Troubleshooting Quantum-Safe SSH – Option 1
Problem: “Permission denied (publickey)”
Solution:
# Check local key permissions
ls -la ~/.ssh/
# Ensure correct permissions
chmod 700 ~/.ssh
chmod 600 ~/.ssh/admin_prod_ed25519
chmod 644 ~/.ssh/admin_prod_ed25519.pub
# Verify key is on server
ssh admin@203.0.113.1 "cat ~/.ssh/authorized_keys"Problem: “sshd refuses to start”
Solution:
# On the server, test configuration
sudo sshd -t
# Check what's wrong
sudo systemctl status sshd
# View logs for error details
sudo journalctl -u ssh -n 20Problem: “Connection using unsupported key exchange algorithm”
Solution:
- Verify both client and server support sntrup761
- Check that sshd was restarted after configuration change
- Verify configuration file was saved correctly
OPTION 2: Quantum-Safe SSH With Compliance – OpenSSH 10.0 NIST ML-KEM
What Is This Quantum-Safe SSH Option?
According to NIST’s official announcement in August 2024 (https://www.nist.gov/), OpenSSH 10.0 was released with support for mlkem768x25519-sha256—combining NIST-standardized ML-KEM-768 with X25519. This represents compliance with the latest cryptographic standards for quantum-safe SSH.
When to use quantum-safe SSH with NIST compliance:
- Your contracts require NIST-standardized algorithms
- You work in government, finance, or healthcare
- Your security policy mandates FIPS compliance
- You want to align with NSM-10 (federal mandate for quantum-safe SSH)
Important Prerequisites for NIST Quantum-Safe SSH
- Ubuntu 24.04 LTS or compatible Linux
- Console access (IPMI/KVM) or another way to connect if SSH breaks
- Root/sudo access
- 2-4 hours for implementation
- Test in non-production first if possible
NIST Quantum-Safe SSH Step-by-Step Implementation
STEP 1: Backup Current Quantum-Safe SSH Configuration
Before making changes, save your current SSH setup:
sudo cp /etc/ssh/sshd_config /etc/ssh/sshd_config.backup.$(date +%Y%m%d)
sudo cp -r ~/.ssh ~/.ssh.backup.$(date +%Y%m%d)STEP 2: Install Required Build Tools for Quantum-Safe SSH
sudo apt update
sudo apt install -y build-essential zlib1g-dev libssl-dev libpam0g-dev libselinux1-dev libwrap0-dev libedit-dev libbsd-dev autoconf automake libtool pkg-config wgetWhat this does: Installs the tools needed to compile OpenSSH 10.0 with quantum-safe SSH from source.
STEP 3: Download OpenSSH 10.0 for Quantum-Safe SSH
cd /tmp
wget https://cdn.openbsd.org/pub/OpenBSD/OpenSSH/portable/openssh-10.0p1.tar.gz
tar -xzf openssh-10.0p1.tar.gz
cd openssh-10.0p1What this does: Downloads and unpacks the latest OpenSSH 10.0 source code with quantum-safe SSH support.
STEP 4: Stop SSH Service (Critical!)
sudo systemctl stop sshd⚠️ WARNING: After this command, you cannot SSH into the server until Step 7. Make sure you have console access or keep an existing SSH window open.
STEP 5: Compile and Install OpenSSH 10.0 for Quantum-Safe SSH
./configure --prefix=/usr \
--sysconfdir=/etc/ssh \
--with-pam \
--with-selinux \
--with-privsep-path=/var/lib/sshd/ \
--with-pid-dir=/run
make
sudo make installThis takes 5-10 minutes. You’ll see a lot of output. That’s normal.
What this does: Compiles OpenSSH 10.0 with NIST quantum-safe SSH algorithms enabled.
STEP 6: Verify OpenSSH 10.0 Installation with Quantum-Safe SSH
ssh -VShould show: OpenSSH_10.0p1
Check for NIST quantum-safe SSH ML-KEM:
ssh -Q kex | grep mlkemShould show: mlkem768x25519-sha256
STEP 7: Configure OpenSSH 10.0 for NIST Quantum-Safe SSH Compliance
sudo nano /etc/ssh/sshd_configAdd or modify these quantum-safe SSH lines:
# NIST-approved post-quantum key exchange for quantum-safe SSH
KexAlgorithms mlkem768x25519-sha256,sntrup761x25519-sha512@openssh.com,curve25519-sha256
Ciphers chacha20-poly1305@openssh.com,aes256-gcm@openssh.com,aes256-ctr,aes128-gcm@openssh.com,aes128-ctr
MACs hmac-sha2-512-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512,hmac-sha2-256
HostKeyAlgorithms ssh-ed25519,rsa-sha2-512,rsa-sha2-256
PubkeyAuthentication yes
PasswordAuthentication no
ChallengeResponseAuthentication no
UsePAM yes
PubkeyAcceptedAlgorithms ssh-ed25519,rsa-sha2-512,rsa-sha2-256
PermitRootLogin prohibit-password
MaxAuthTries 3
LoginGraceTime 30STEP 8: Test and Restart Quantum-Safe SSH
sudo sshd -t
sudo systemctl restart sshd
sudo systemctl status sshdSTEP 9: Verify NIST Quantum-Safe SSH ML-KEM
ssh -v admin@localhost 2>&1 | grep "kex:"Should show: debug1: kex: algorithm: mlkem768x25519-sha256
OPTION 3: Maximum Quantum-Safe SSH Security Using OQS-OpenSSH
What Is This Quantum-Safe SSH Option?
According to the Open Quantum Safe project documentation (https://openquantumsafe.org/) at the University of Waterloo, OQS-OpenSSH provides both post-quantum key exchange and post-quantum signatures through algorithms like ML-DSA (Dilithium). This provides maximum quantum-safe SSH protection through hybrid classical and quantum-resistant protection.
Important: This is research code. Use OQS-OpenSSH for learning and testing only, not production infrastructure.
Prerequisites for OQS Quantum-Safe SSH
- Ubuntu 24.04 LTS or similar
- Console access (IPMI/KVM)
- Comfortable with command-line
- 4-8 hours for implementation
- Test environment only for OQS
Quick OQS Quantum-Safe SSH Implementation
STEP 1: Install Dependencies for OQS Quantum-Safe SSH
sudo apt update
sudo apt install -y autoconf automake cmake gcc git libtool libssl-dev make ninja-build zlib1g-devSTEP 2: Compile liboqs for Quantum-Safe SSH
cd /tmp
git clone --depth 1 --branch 0.13.0 https://github.com/open-quantum-safe/liboqs.git
cd liboqs && mkdir build && cd build
cmake -GNinja -DCMAKE_INSTALL_PREFIX=/opt/liboqs ..
ninja
sudo ninja installSTEP 3: Compile OQS-OpenSSH for Maximum Quantum-Safe SSH
cd /tmp
git clone --depth 1 --branch OQS-v9 https://github.com/open-quantum-safe/openssh.git
cd openssh
./configure --prefix=/opt/oqs-openssh \
--with-libs=-loqs \
--with-cflags="-I/opt/liboqs/include" \
--with-ldflags="-L/opt/liboqs/lib"
make
sudo make installSTEP 4: Generate Hybrid Quantum-Safe SSH Key
/opt/oqs-openssh/bin/ssh-keygen -t ssh-ed25519-dilithium2 -a 200 -f ~/.ssh/admin_hybrid_pq -C "admin@company.com_$(date +%Y-%m-%d)" -oThis creates a quantum-safe SSH key protected by both classical (Ed25519) and quantum-resistant (Dilithium2) algorithms.

Quick Decision Guide: Which Quantum-Safe SSH Option Is Right For You?
Not sure which quantum-safe SSH option to choose? Use this:
Choose Option 1 (Quantum-Safe SSH 9.6) if:
- You want the easiest quantum-safe SSH implementation
- You’re not required to use NIST algorithms
- You want automatic security updates
- You want zero maintenance
Choose Option 2 (Quantum-Safe SSH 10.0 NIST) if:
- You work in government/finance/healthcare
- Your contracts require NIST quantum-safe standards
- You can handle manual updates
- Compliance matters more than simplicity
Choose Option 3 (OQS Quantum-Safe SSH) if:
- You’re researching post-quantum cryptography
- You have a test environment
- You want maximum theoretical quantum-safe protection
- You accept experimental status

General Quantum-Safe SSH Security Practices (All Options)
Passphrase Security (Critical for Quantum-Safe SSH!)
Your passphrase is the key that protects your private quantum-safe SSH key. Make it strong:
- Minimum 20 characters (recommend 24-32)
- Mix it up: Uppercase, lowercase, numbers, symbols
- Example:
Quantum-Safe2025@XOOMMIT!#ServerProd - Store in: Password manager only (never plain text)
Weak passphrases defeat the entire purpose of quantum-safe SSH encryption.
Key Rotation Strategy for Quantum-Safe SSH
Change your quantum-safe SSH keys periodically:
- Critical systems: Every 60 days
- Production servers: Every 90 days
- Development: Every 180 days
- Suspected breach: Immediately
Monitoring SSH Access for Quantum-Safe Infrastructure
Track who’s accessing your servers:
# View SSH logs
tail -f /var/log/auth.log | grep sshd
# Look for suspicious patterns
sudo grep "Failed password" /var/log/auth.log
sudo grep "Accepted publickey" /var/log/auth.logFirewall Configuration for Quantum-Safe SSH
Restrict SSH access to trusted networks:
# Ubuntu UFW
sudo ufw allow from 203.0.113.0/24 to any port 22
sudo ufw enable
# Fedora/RHEL firewalld
sudo firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="203.0.113.0/24" port port="22" protocol="tcp" accept'
sudo firewall-cmd --reloadNever expose SSH directly to the internet without restrictions.
Real-World Quantum-Safe SSH Troubleshooting
Common Issue 1: “Permission denied (publickey)”
What this means: The server won’t accept your quantum-safe SSH key.
How to fix it:
# 1. Check your local key permissions
ls -la ~/.ssh/
# Should show: -rw------- (600) for private key
# 2. Fix permissions if needed
chmod 700 ~/.ssh
chmod 600 ~/.ssh/admin_prod_ed25519
chmod 644 ~/.ssh/admin_prod_ed25519.pub
# 3. Verify key is on the server
ssh admin@server "cat ~/.ssh/authorized_keys"
# 4. Compare with your public key
cat ~/.ssh/admin_prod_ed25519.pub
# They should matchCommon Issue 2: “sshd refuses to start”
What this means: Your quantum-safe SSH configuration has a syntax error.
How to fix it:
# 1. Test configuration syntax
sudo sshd -t
# Shows error and line number if wrong
# 2. Check what's running
sudo systemctl status sshd
# 3. View recent logs
sudo journalctl -u ssh -n 20
# 4. Fix the error shown, then test againCommon Issue 3: “Connection using unsupported key exchange algorithm”
What this means: Client and server don’t agree on quantum-safe SSH algorithms.
How to fix it:
# 1. Check what your client supports
ssh -Q kex
# 2. Check what your server supports (on server)
ssh -Q kex
# 3. Look for sntrup or mlkem in both lists
# If missing from either, that's the problem
# 4. Verify sshd was restarted after configuration change
sudo systemctl restart sshd
Organizational Compliance Reference for Quantum-Safe SSH
| Organization Type | Recommended Option | Why |
|---|---|---|
| Small Business | Option 1 | Simple to implement, automatic updates |
| Startup | Option 1 | Fast deployment, minimal overhead |
| Enterprise | Option 1 or 2 | Option 1 for general use, Option 2 if regulated |
| Financial Services | Option 2 | NIST compliance mandatory |
| Healthcare | Option 2 | HIPAA long-term data protection |
| Government Contractor | Option 2 | NSM-10 federal mandate |
| Research Lab | Option 3 | Post-quantum cryptography testing |
| Cloud Provider | Option 2 | Industry standard alignment |
Why You Must Implement Quantum-Safe SSH Now
Let’s be direct: waiting isn’t an option for quantum-safe SSH adoption. Here’s why immediate adoption of quantum-safe SSH isn’t a nice-to-have—it’s a critical business decision.
The Time Factor for Quantum-Safe SSH Implementation
You have approximately 8-10 years before quantum computers become powerful enough to decrypt archived SSH sessions. That sounds like enough time. It isn’t. Here’s why for quantum-safe SSH:
First, the immediate window is shorter: If adversaries are harvesting encrypted sessions today, data transmitted in 2025 becomes vulnerable starting around 2030. That’s 5 years. Five years for you to audit all quantum-safe SSH infrastructure, migrate to quantum-resistant algorithms, rotate all SSH keys, update deployment automation, train your team, test in production, and handle exceptions. For large organizations, this is genuinely challenging on a 5-year quantum-safe SSH timeline.
Second, retroactive exposure is permanent: Unlike traditional security incidents where you can fix a vulnerability and move forward, quantum decryption of historical archives creates permanent exposure. Data stolen through quantum decryption in 2033 doesn’t get un-stolen. Competitive advantages don’t become confidential again. Customer data doesn’t go back into your control. This is why quantum-safe SSH now beats encryption later.
The Regulatory Reality for Quantum-Safe SSH
Regulatory requirements for quantum-safe SSH aren’t waiting. They’re arriving:
- U.S. National Security Memorandum (NSM-10) at (https://www.whitehouse.gov/) mandates federal agencies transition to quantum-safe SSH and cryptography by 2030
- Financial Regulatory Authority increasingly requiring quantum-safe SSH for long-term data protection
- HIPAA at (https://www.hhs.gov/hipaa/) expanding to include quantum-safe SSH requirements for healthcare data
- EU Cybersecurity Act at (https://digital-strategy.ec.europa.eu/) mandating quantum-safe SSH assessment for critical infrastructure
- Industry Standards (ISO, NIST) establishing quantum-safe SSH baselines
If you wait until regulations become mandatory, you’ll be implementing quantum-safe SSH under time pressure with compliance penalties hanging over you. If you implement quantum-safe SSH now, you’re ahead of requirements.
The Competitive Advantage of Early Quantum-Safe SSH Adoption
Organizations that adopt quantum-safe SSH first gain:
Security Leadership: Marketing your quantum-safe SSH infrastructure to customers and partners
Regulatory Moat: Early quantum-safe SSH compliance means you’re ready when regulations arrive
Customer Trust: Demonstrating long-term data protection with quantum-safe SSH builds confidence
Insurance Benefits: Many cyber insurance policies offer premium reductions for quantum-safe SSH deployment
Talent Attraction: Security-conscious engineers want to work on quantum-safe SSH infrastructure

The True Cost of Delaying Quantum-Safe SSH
Each year you delay quantum-safe SSH implementation:
- Risk window shrinks while migration timeline stays same-length
- Regulatory requirements for quantum-safe SSH tighten
- Adversaries harvest more of your sessions
- Technical debt accumulates
- Team knowledge becomes outdated
Starting quantum-safe SSH now means:
- Gradual, planned migration instead of rushed emergency response
- Time to test thoroughly before production deployment
- Ability to train team systematically
- Opportunity to bake quantum-safe SSH into your architecture
- Buffer to handle unexpected complications
The Implementation Reality of Quantum-Safe SSH
Here’s the honest assessment: none of the three quantum-safe SSH options is dramatically difficult:
Option 1 (9.6): Literally just update your packages and modify configuration files. If your organization can’t handle quantum-safe SSH at this level, bigger problems exist.
Option 2 (10.0): Requires compilation, but the quantum-safe SSH process is straightforward. Any infrastructure team that manages kernel updates can handle this.
Option 3 (OQS): Experimental, yes. But great for testing and learning quantum-safe SSH. Perfect for preparing your organization’s understanding.
The question isn’t “Can we implement quantum-safe SSH?” It’s “Why haven’t we done this yet?”
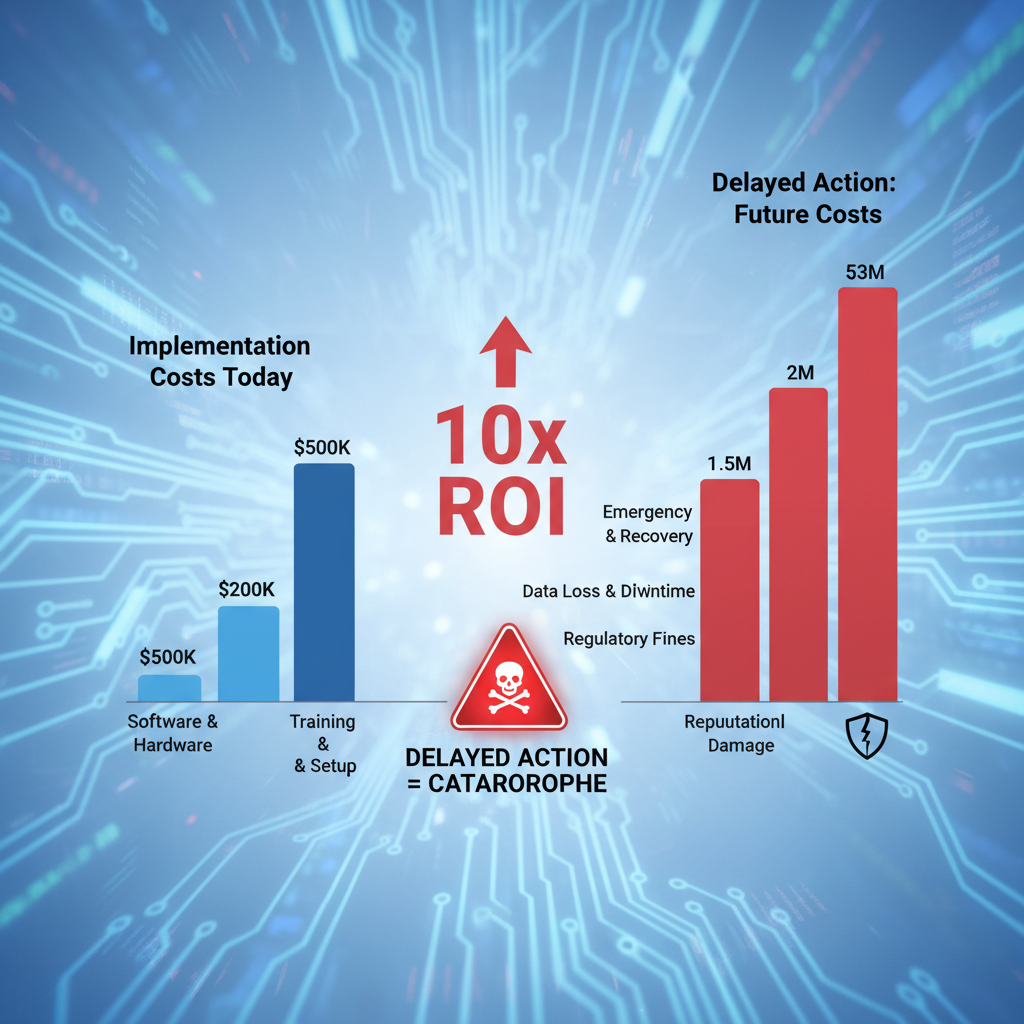
The Risk Calculation for Quantum-Safe SSH
Let’s do the math simply about quantum-safe SSH:
Cost of implementing quantum-safe SSH today:
- Option 1: 4-8 hours (free)
- Option 2: 8-16 hours (free, manual maintenance cost)
- Option 3: 20-40 hours (free, experimental)
Cost of quantum decryption of 2025-2026 SSH sessions later:
- Data exposure: Potentially millions in damages
- Regulatory fines: Millions more
- Reputational damage: Years of recovery
- Customer churn: Significant revenue loss
- Legal liability: Class action lawsuits potential
The risk-reward calculation for quantum-safe SSH is stark: small implementation cost now versus massive potential cost later.
External Resources and Further Reading on Quantum-Safe SSH
Official Documentation on Quantum-Safe SSH:
- NIST Post-Quantum Cryptography Standards: https://csrc.nist.gov/Projects/post-quantum-cryptography/
- OpenSSH Release Notes and Quantum-Safe SSH: http://www.openssh.com
- Open Quantum Safe Project Documentation: https://openquantumsafe.org/
Government Standards for Quantum-Safe SSH:
- NSM-10 Memorandum: Advancing Quantum-Safe Cryptography: https://www.whitehouse.gov/
- CISA Post-Quantum Cryptography Migration Guidance: https://www.cisa.gov/
- NIST Special Publication 800-227: Post-Quantum Cryptography and Quantum-Safe SSH: https://csrc.nist.gov/publications/detail/sp/800-227/final
Technical Papers on Quantum-Safe SSH:
- “Harvest Now, Decrypt Later” Threat Analysis: IEEE Transactions on Information Theory
- Journal of Cryptology: Post-Quantum Algorithm Analysis and Quantum-Safe SSH
- ACM Computing Surveys: Quantum Computing Threat Assessment
Industry Resources for Quantum-Safe SSH:
- Linux Foundation Cybersecurity Report 2024: https://www.linuxfoundation.org/
- McKinsey Quantum Risk Assessment and Quantum-Safe SSH: https://www.mckinsey.com/
- Ponemon Institute: Quantum Decryption Threat Analysis: https://www.ponemon.org/
Final Conclusion: The Time for Quantum-Safe SSH Is Now
This isn’t about being paranoid. This is about basic risk management with quantum-safe SSH.
The Math on Quantum-Safe SSH:
- Time until quantum computers break your encryption: 5-10 years
- Time needed to migrate SSH infrastructure: 5-10 years
- Window left for gradual quantum-safe SSH migration: Zero
The Business Case for Quantum-Safe SSH:
- Cost to implement quantum-safe SSH now: A few hours of setup (free if Option 1)
- Cost to implement quantum-safe SSH under emergency pressure: Millions in rushed deployment
- Cost of quantum decryption of 2025 data: Potentially $50M+ in damages
Your Action Items for Quantum-Safe SSH:
- This week: Choose Option 1 or 2 based on your requirements
- This month: Implement quantum-safe SSH on a test system first
- This quarter: Roll out quantum-safe SSH to production infrastructure
- Going forward: Maintain quantum-safe SSH practices in all new deployments
The adversaries recording your SSH sessions today aren’t waiting. The quantum computers aren’t waiting. Your infrastructure security shouldn’t be waiting either.
Start with Option 1 quantum-safe SSH today. It takes 30 minutes. You can implement it right now.
Your future security depends on the decision you make today regarding quantum-safe SSH. Make it count.
Next Steps for Quantum-Safe SSH Implementation
- Read this quantum-safe SSH guide completely (you’re doing great so far!)
- Choose your quantum-safe SSH option (most people choose Option 1)
- Test on a non-critical server first
- Follow the quantum-safe SSH step-by-step implementation
- Verify it’s working using the verification steps
- Roll out to production gradually
- Document your quantum-safe SSH changes for your team
You’ve got this. Quantum-safe SSH is within reach.
Quick Reference Summary for Quantum-Safe SSH
Most Important Information for Quantum-Safe SSH:
| Aspect | Option 1 | Option 2 | Option 3 |
|---|---|---|---|
| Setup Time | 30 min | 2-4 hours | 4-8 hours |
| Maintenance | Automatic | Manual | Manual |
| Compliance | Partial | Full NIST | Experimental |
| Best For | Everyone | Government/Finance | Research |
Implementation Status Checklist for Quantum-Safe SSH:
- ☐ Option chosen
- ☐ Environment prepared
- ☐ Configuration created
- ☐ Keys generated
- ☐ Server configured
- ☐ Tested successfully
- ☐ Deployed to production
- ☐ Verified working
- ☐ Team trained
- ☐ Documented